 The first and foremost feature of an IBM DataPower is as a security device. However, most organizations turn their Datapower over to their security team and ignore it afterwards. The security team(s) generally use it as a perimeter security device – as a firewall and filter for exposing SOA services out to the Internet (or via VPN connections, as who can trust a vendor’s network anymore). It works in this capacity very well but is far more capable than just this narrow role.
The first and foremost feature of an IBM DataPower is as a security device. However, most organizations turn their Datapower over to their security team and ignore it afterwards. The security team(s) generally use it as a perimeter security device – as a firewall and filter for exposing SOA services out to the Internet (or via VPN connections, as who can trust a vendor’s network anymore). It works in this capacity very well but is far more capable than just this narrow role.
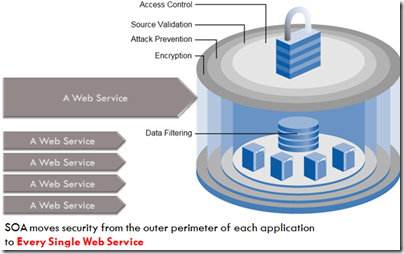 With SOA breaking down the outer perimeter of our internal applications, security must now be layered and extended to EVERY exposed service or interface. There’s two general approaches to providing this: The agent based model, where an agent is installed upon every server / application / application container and controls access to each service. The other is an agentless model, where each web service is routed through a control point – in this case the Datapower, and the control point provides the agent management capabilities. The Datapower makes an excellent agentless control point due to it’s extensive security capabilities and it’s speed. Further, many SOA governance and service management applications have integrated with the Datapower as their control-agent.
With SOA breaking down the outer perimeter of our internal applications, security must now be layered and extended to EVERY exposed service or interface. There’s two general approaches to providing this: The agent based model, where an agent is installed upon every server / application / application container and controls access to each service. The other is an agentless model, where each web service is routed through a control point – in this case the Datapower, and the control point provides the agent management capabilities. The Datapower makes an excellent agentless control point due to it’s extensive security capabilities and it’s speed. Further, many SOA governance and service management applications have integrated with the Datapower as their control-agent.
As an enterprise IT shop realizes the real exposure that has occurred as they’ve moved to a full integration pattern, providing full web service security becomes imperative. On a side note, this problem is not limited to web services. It exists as well for stored procedures as well as MQ (or TIBCO) messaging. Generally the concern for those has been lower (because stored procedures have database level security by default and messaging protocols are difficulty to of use and obscure enough to avoid notice by the average attacker). The Datapower can provide security for them as well.
Therefore wrapping the Datapower in as a full internal web service control point is strongly recommended. Other alternatives (such as Amberpoint) are very viable solutions as well.
More on what Datapower security features make sense in an average IT shop in a future article.
(Why am I going into the Datapower? Because I’ve had the opportunity to do a project with one and had an incredibly hard time finding any valuable architecture information on it. Basic features are clear, how to fit it into your enterprise integration model – not so much.)

